We’ve come a long way since the days of two keys for a car. One unlocked the door, the other turned the engine over. The good ol’ days …
We digress. Many brands have expressed interest in turning the smartphone into a driver’s set of car keys and now Ford has filed its own patent for a solution. Ford Authority reported on the patent this Wednesday, which describes a smartphone case that turns the phone into a functional key fob.
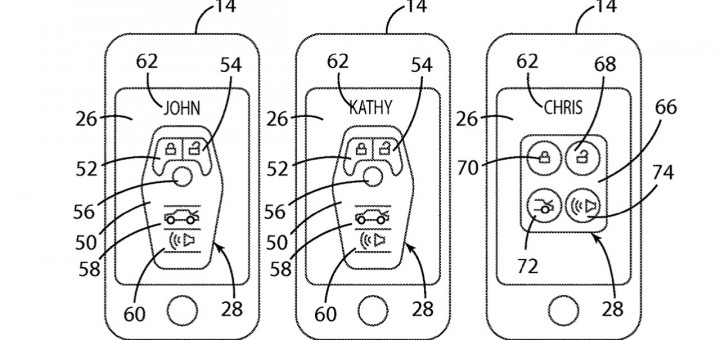
With the case, the phone would communicate via Bluetooth or NFC (near-field communication) and the patent image shows the keyfob itself on the phone’s screen. Lock, unlock, truck and other commands are present. The best feature is probably the possibility of the case turning a smartphone into a proximity key, which would unlock the car once the driver approaches the car.
BMW has proposed a similar solution and Polestar has previously detailed its own phone-as-key technology that will be available with its car-subscription plan.
We haven’t heard much from General Motors on the matter, but it doesn’t seem unlikely that the automaker won’t pursue this route. Users can already access vehicle commands via their smartphone with brand-specific apps. Cadillac will even let drivers start their cars with an Apple Watch. Ditto for Chevrolet.
Would you like to have your phone double as a car key? Talk to us below.














Comments
NFC, Bluetooth, and Wi-Fi hackers have already shown us how easy it is to trick a car into thinking that the thief has the key. If so, then it is going to become easier to steal cars. We’re going backwards.
GM already offers a phone as a key. I rented a Malibu from Maven a few months ago my iPhone was the key.
No. I prefer a physical key that is “unhackable”. As an EE I love pioneering technology, but not anything that reduces security.
What happens if the smartphone is lost, damaged, or just runs out of battery charge? How will the owner open and run the vehicle? If you need a backup key (as in the Chevy Volt and Bolt EVs) then why go through the trouble of using a smartphone at all?
“No. I prefer a physical key that is “unhackable””
Lockpicking is hacking. Nothing is unhackable.
Try hacking a hiccup
Not just two keys, some older cars had a third key for the trunk as well. I agree with Raymondjram , what if the cars battery is dead and you can’t get the door open. How would you access the hood release in order to jumpstart your car.
If it were equipped with one of those old school gasoline engines?
You make good point there fastyle. Around 85 or 86 friend of mine bought himself a Monte Carlo SS. Had a security system installed which included an electric hood release. That seems like a good idea at the time. But when his battery went dead he had to crawl underneath the car to hook up the Positive jumper cable to the positive battery cable on the starter.
The article doesn’t mention that this already exists in the real world. Not just for renting a car either like someone above me mentioned with Maven. The Tesla Model 3 can be unlocked with your smartphone as the key or you have a keycard to unlock it that is the size of a credit card.
Makes you wonder what exactly Ford has changed or improved to get their own patent?
Gm already has this
Chevrolet already has an App that will allow owners of an Apple iPhone to remote start their vehicle.
http://gmauthority.com/blog/gm/general-motors-technology/general-motors-apps/mychevrolet-mobile-app/
Anyone ever have trouble getting a reliable signal from their cell carrier, even during good weather? And what of major storms that may disable cell towers for days or weeks? Even though we may have functional cars, without functional cell service, we cannot use our vehicles to get out of harms way? Sounds like there are still a lot of non-technical, non-automotive safety issues yet to consider, in addition to hackers and security.